Traffic between your device and your Cloud Solution is encrypted to protect your data during transport. But in some cases you want to debug your code and inspect network packets. In this tutorial, I will show you exactly how to decrypt traffic between your IoT-device and a cloud solution like Azure IoT Hub or AWS IoT Core. Both solutions use TLS to protect communication whereby this tutorial is applicable to every TLS connection initiated by NodeJs.
Cipher Suites and Perfect Forward Secrecy
AWS recommends Cipher Suites like ECDHE-ECDSA-AES128-GCM-SHA256 with an ECDHE Key Exchange Algorithm which has the Perfect Forward Secrecy (PFS) feature. Therefore, session keys will not be compromised even by capturing the private key because of a new set of Diffie-Hellmann parameters generated upon every session. This means, that even with the private key, we are not able to see plain communication. Therefore, we need to ensure the use of a weaker Cipher Suite without PFS, if you have the private key.
Cipher Suite downgrade
In order to decrypt the packets with the private key, you need to downgrade the Cipher Suite to one, which doesn’t use ECDHE as Key Exchange Algorithm. This is because of the PFS feature stated here. On the official website of Amazon Web Services is a list of all supported Suites. Now choose one without ECDHE like AES128-SHA which uses RSA as Key Exchange Algorithm. This option alone only works, when you are in possession of the used private key.
TLS Keylog File
How do we retrieve the decryption key now? If you get your hands on the private key used by Amazon or Microsoft, you are able to decrypt packets but that is rather unlikely. The next best thing is the session key used for encrypting the packets. This is possible by logging information about that key during communication in a keylog file. This file is loaded later into Wireshark to decrypt traffic. In the following step we look at the decryption process with NodeJs.
NodeJs TLS keylog file
At first we assume iot-device.js is the file containing device logic. Now you pass the parameter tls-cipher-list=”<cipher-suite>” to select a supported cipher suite without ECDHE. With tls-keylog=”<path>” you specify the path for the keylog file. Afterward start listening with Wireshark to capture the traffic and start your code on the device with the following command. These parameters are available since NodeJs version 12 ! Note, you don’t need to use a weaker cipher suite and the tls-cipher-cipher argument, if you use the tls-keylog option.
node --tls-cipher-list="AES128-SHA" --tls-keylog=$(pwd)/keylog.txt iot-device.jsDuring execution and after the TLS connection is established the session key is logged in keyfile.txt. Now you can load the keylog.txt in Wireshark and decrypt traffic.
TLS decryption in Wireshark with keylog file
During execution and after the TLS connection is established the session key is logged in keyfile.txt. Now you can load the keylog.txt in Wireshark.
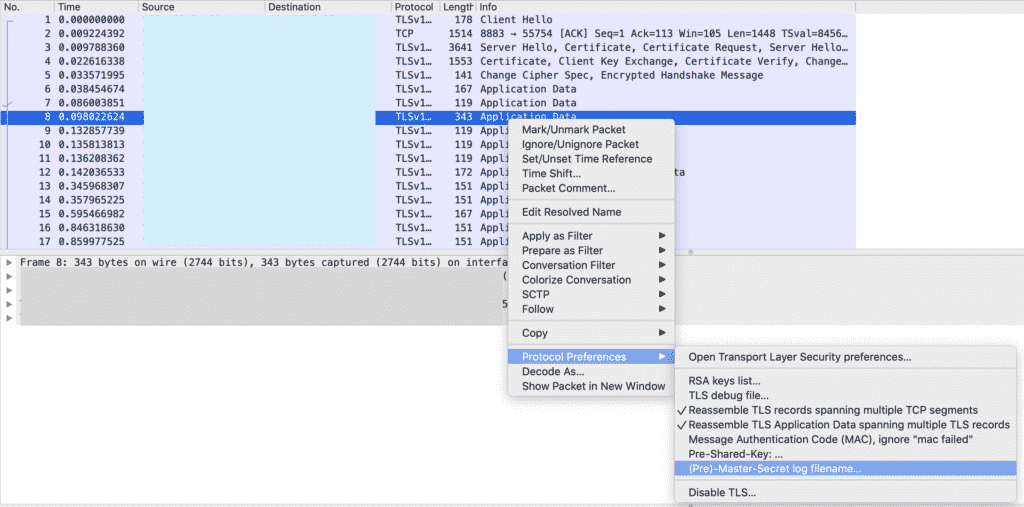
In Wireshark you can filter the TLS traffic with “tls” filter option. Next, you right-click an encrypted TLS packet and click on “Protocol Preferences” > “(Pre)-Master-Secret log filename…” and choose the keylog file in the following dialog.
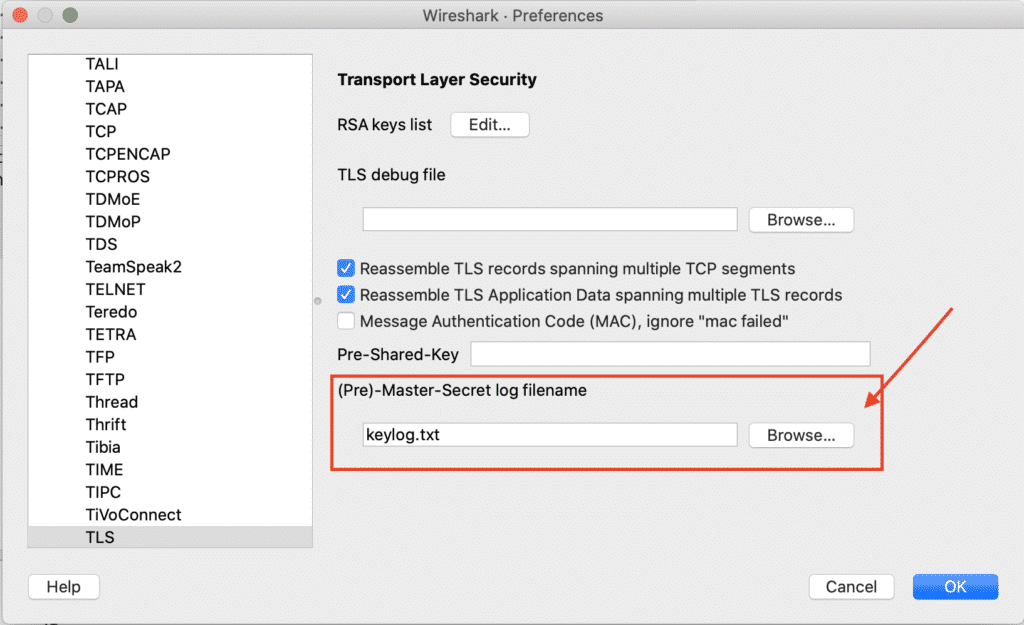
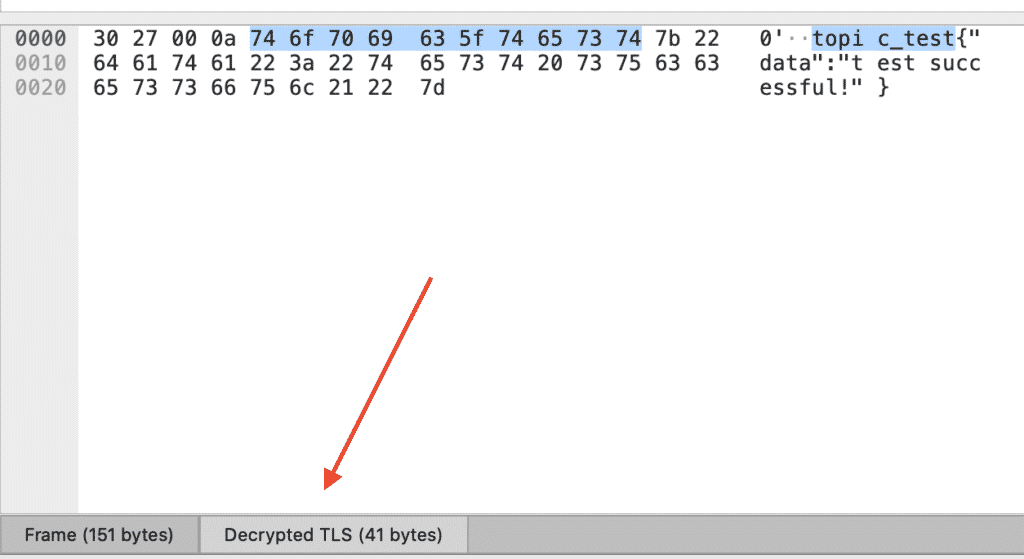
Now you can inspect decrypted messages between your IoT-device and your Cloud Solution by clicking on “Decrypted TLS” at the bottom.
Conclusion
As you can see with a few tweaks it is possible to view and debug encrypted traffic between your device and the cloud. If you have trouble following this tutorial please feel free to leave a comment below and I will answer as fast as possible.
If you are interested in how I started this blog, you can check out my previous Post.






Stunning story there. What occurred after? Good luck!
I see no “Decrypted TLS” tab in the bottom 🙁